Best Practices of Secrets Management with Kubernetes

Unlock the potential of your Kubernetes deployments by mastering the best practices for managing secrets, as today’s recent data breaches prove that robust secret management and security are paramount.
Thinking in terms of security with Kubernetes
Kubernetes External Secrets offer an alternative approach to managing secrets, enabling organizations to leverage external secret management systems.
More advanced features and security mechanisms are unlocked by external secret management systems, including robust encryption, access control, and audit capabilities, enhancing the overall security of secrets and centralizing their management for consistency and reduced complexity across multiple Kubernetes clusters.
- Kubernetes External Secrets enable integration of external secret management systems (e.g., HashiCorp Vault, AWS Secrets Manager).
- External Secrets act as a bridge between Kubernetes and external secret management systems.
- Secrets are not stored directly within the Kubernetes cluster, which provides advantages over storing them inside Kubernetes.
One more robust mechanism for additional security is Role-Based Access Control (RBAC) which can significantly enhance secret management practices.
RBAC complements encryption by limiting access to secrets to only those entities with the appropriate permissions, reducing the attack surface and minimizing the risk of accidental exposure. Combining encryption, RBAC and External Secrets in Kubernetes enhances secret management by providing multiple layers of defense.
RBAC best practices
Implementing encryption and RBAC effectively requires following several best practices, including:
- Regularly rotating encryption keys
- Utilizing strong encryption algorithms
- Adopting secure key management practices.
- Regularly review and update RBAC policies to align with changing access requirements and ensure that the principle of least privilege is maintained throughout the cluster.
Encryption ensures that even if unauthorized access to secrets occurs, the encrypted data remains unreadable without the corresponding decryption keys.
Secrets Lifecycle in Kubernetes
In Kubernetes secrets management, secrets can be created, used, updated, and deleted through a set of intuitive and well-defined operations.
The Kubernetes API provides a straightforward approach to managing secrets within a cluster.
Creating a Secret in Kubernetes
To create a secret in Kubernetes, administrators can use the kubectl command-line tool or interact with the Kubernetes API directly.
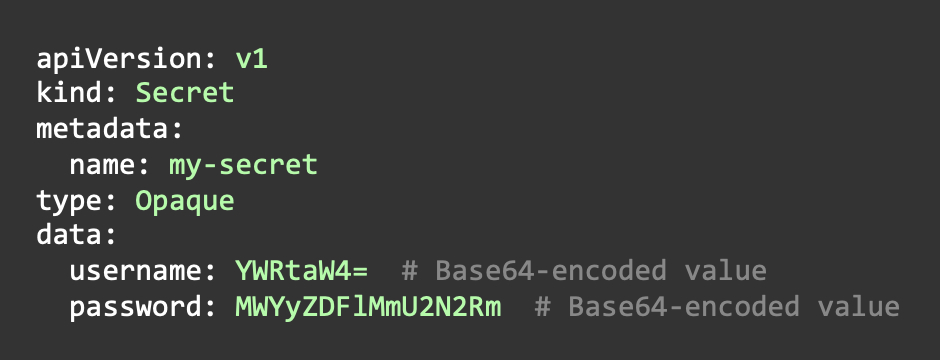
Secrets are typically created from YAML files that define the secret’s metadata and data fields.
The data fields contain sensitive information, which is base64-encoded to ensure proper encoding and decoding when used by applications. Once the YAML file is defined, it can be applied to the cluster, and the secret will be created.
Applying a Secret
Once a secret is created, it can be used by applications running within the Kubernetes cluster.
Pods can access secrets either through environment variables or as mounted files. When using environment variables, the values are injected into the pod’s environment, allowing applications to access them directly.
Alternatively, secrets can be mounted as files, which enables applications to read the secret values from specific file paths.
Updating a Secret
Updating secrets in Kubernetes involves modifying the existing secret object. Administrators can update the secret’s data fields by applying changes to the secret’s YAML file and reapplying it to the cluster.
It’s important to note that when updating secrets, the new values must be base64-encoded before applying the changes.
Deleting a Secret
When it comes to deleting secrets, administrators can use the kubectl delete command or the Kubernetes API to remove the secret object from the cluster. Once deleted, the secret is immediately unavailable to any application or entity that previously had access to it.
An example of deletion of a secret using ‘kubectl’ could look like this.
kubectl delete secret my-secret
In addition, secrets stored on the cluster are typically base64-encoded, and are not encrypted, making them vulnerable to attackers by simply decoding and accessing the secrets.
It would be advised to always consider a well-rounded security solution, that can enable and empower the Kubernetes cluster admin teams to keep track of logs, IAM activity and secrets usage from a central perspective.
Entro Security Platform is an example of such a tool that continuously monitors and scans all the security resources of the cluster and is able to detect anomalous activity.
Best Practices in Secrets Management in Kubernetes
To implement best practices for Kubernetes secrets management, readers can take the following steps:
- Employ encryption: encrypt the secrets stored within the external secret management system.
Utilize encryption mechanisms to protect secrets at rest and in transit.
Leverage secret providers or external key management systems for enhanced encryption capabilities, especially when the secrets are stored in external systems that may be accessed by multiple entities
- Implement RBAC: Define fine-grained Role-Based Access Control (RBAC) policies to limit access to secrets based on roles and responsibilities. Regularly review and update RBAC policies to align with evolving access requirements. Within that make sure to establish strong non human identity management protocols.
- Regularly rotate secrets: Compliance requirement states the need to establish a policy and process for regularly rotating secrets stored in the external secret management system. Automate the rotation process wherever possible to ensure timely updates and minimize manual errors.
- Secrets segregation: Carefully consider the scope and granularity of secrets when configuring External Secrets. Avoid bundling multiple unrelated secrets together, as it can increase the attack surface and complicate management. Instead, segregate secrets based on their purpose or application to minimize risk.
- Monitor and audit: Implement logging and monitoring mechanisms to track access to secrets and detect any suspicious activity. Regularly review logs and establish alerting mechanisms to respond to security incidents promptly. A Good way at achieving these goals are through effective identity management, ensuring that only authorized users have access to secrets.
IAM policies can be utilized to control and manage access to secrets based on specific user roles and permissions.
Privileged access management can be implemented to restrict elevated access to secrets, ensuring that only authorized individuals can manage them. Additionally, cloud entitlement management plays a crucial role in defining and managing entitlements for different users and roles, ensuring proper access controls are in place for secrets.
- Automate secret distribution: Leverage Kubernetes native mechanisms, such as environment variables or mounted files, to automate the distribution of secrets to relevant components. Automation improves consistency, reduces human error, and simplifies secret management.
- Follow secure practices: Avoid storing secrets in plain text, use strong encryption algorithms, and adhere to secure key management practices. Regularly assess and update security configurations to address emerging threats.
- External Secret Management – Storing secret keys externally from the Kubernetes cluster, using a secrets manager, offers multiple benefits: enhanced protection by reducing exposure and limiting access to secrets only at the application’s runtime, easier rotation of secrets as they are external to the cluster thus eliminating downtime, and added abstraction through a centralized, secure repository for secret storage and access.
Gotchas and Common Mistakes When Managing Secrets In Kubernetes
While Kubernetes provides robust capabilities for managing secrets, there are some common pitfalls that organizations should be aware of and avoid to ensure effective secret management. By understanding and addressing these potential mistakes, organizations can enhance the security of their Kubernetes clusters.
- One common mistake to avoid is storing secrets in plain text within Kubernetes manifests or configuration files. It is crucial to always ensure proper encryption, as this is the most viable way to properly protect secrets.
Encrypting secrets at rest and in transit provides a more robust layer of protection against unauthorized access.
- Inadequate RBAC policies can also lead to security vulnerabilities. Failing to establish well-defined Role-Based Access Control (RBAC) policies can result in excessive privileges or improper access to secrets. It is essential to carefully define roles, role bindings, and service accounts, granting only the necessary permissions to access and manage secrets. Regularly reviewing and updating RBAC policies ensures alignment with evolving access requirements, removes excessive permissions, and enhances the overall security posture of the Kubernetes secret manager cluster.Moreover, implementing separate namespaces within the cluster is highly recommended to boost security. By utilizing namespaces, access to secrets can be tightly controlled, ensuring that only authorized developers or teams have the necessary access privileges within their designated namespaces, further minimizing the risk of unauthorized access or accidental exposure of secrets.
- Weak secret management practices, such as using default or easily guessable passwords or keys, can compromise the security of secrets. Implementing strong encryption algorithms, regularly rotating encryption keys and secrets, and adopting secure key management practices are essential in maintaining a secure secret management framework.
- Lack of auditing and monitoring can hinder the ability to detect and respond to security incidents. Managing secrets by implementing logging and monitoring mechanisms to track access to secrets, review logs regularly, and establish alerting mechanisms to identify any suspicious activity promptly.
It is advisable to make sure logging is enabled and is being organized in a manner that allows it to gain exposure when the need arises.
A platform like Entro enables one to keep track of the auditing log in a single pane of glass.
- Manual secret distribution can introduce errors and inconsistencies. Leveraging Kubernetes native mechanisms, such as environment variables or mounted files, automates the distribution of secrets to relevant components, ensuring consistency, reducing human error, and simplifying secret management.
- Insufficient secret rotation increases the risk of unauthorized access or compromise. Establish a policy for regular secret rotation and automate the process where possible. This practice helps mitigate the impact of potential breaches and ensures that compromised secrets become obsolete.
A Call to Action
In conclusion, proper Kubernetes secret management is essential in protecting sensitive information, adhere to compliance regulations, and maintain the integrity of applications and data.
By following best practices such as encryption, RBAC, regular rotation, monitoring, automation, and secure practices, organizations can establish a robust foundation for a Kubernetes secrets manager.
Additionally, integrating a holistic security platform like Entro compliments these best practices by providing organizations with the ability to gain full context and understanding of their secrets.
With its cloud-based solution and comprehensive visibility, Entro empowers organizations to efficiently manage secrets, enabling them to make informed decisions, mitigate risks, and strengthen their overall security posture within Kubernetes clusters.
And as always, it is important to remember that with a proactive and diligent approach, organizations can fortify the security of their Kubernetes clusters, safeguard sensitive information, and effectively mitigate the risks associated with unauthorized access or data breaches.
Get updates
All secret security right in your inbox